
Bitcoin march colonialtom robinson ellipticblog
4. Law Enforcement Is Getting Better at Tracking Illicit Crypto Flows, but Challenges Remain
Bitcoin march btc robinson ellipticblog
It is worth noting that earlier today (February 25), someone made a single donation of over $3 million worth of bitcoin to an entity supporting the Ukrainian forces. News & Insights In a clear attempt to maximize the financial gains from the attack, the hackers chose to ask for payments in bitcoin - the most widely used and accessible cryptoasset. Some tweets also asked for payments in Ripple (XRP), but none were received.
Bitcoin network construction
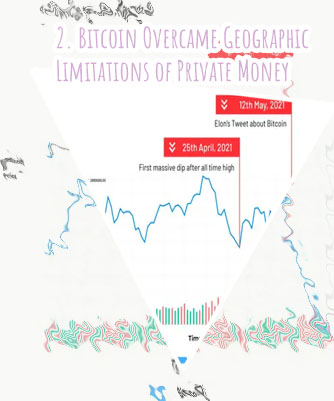
Analysis march btc colonialtom ellipticblog
MBTC: millibitcoin, 0.001 of a bitcoin Investigating Bitcoin Crime: The Battle Against Illicit Use Of Digital Currency | Elliptic The methodology used by Ahn et al. (2016) for the RIF looks at the total number of transactions for each seed address, the total amount of bitcoins sent and received, and the number of ransom payments received. At an individual transaction level, the framework followed the input and output addresses, bitcoins transferred, and timestamps of these transfers. These parameters were used to build the target network model for their research, along with additional labels to indicate the network depth (i.e., how far away from the seed address the activity is taking place) and any service identifiers able to be picked up from a blockchain Application Programming Interface (API) that indicate Bitcoin exchanges.